Stored Cross-Site Scripting
Level: Apprentice
Today we will solve Portswigger’s “Stored XSS into anchor href attribute with double quotes HTML-encoded” lab from their XSS (Cross-site scripting) series.
This is the information that we are starting with:
This lab contains a stored cross-site scripting vulnerability in the comment functionality. To solve this lab, submit a comment that calls the 'alert' function when the comment author name is clicked.
When we open the lab, we see that it’s a blog with different posts. When we open a post, we see a comment functionality. Let’s try adding something random in every field and let’s post the comment:
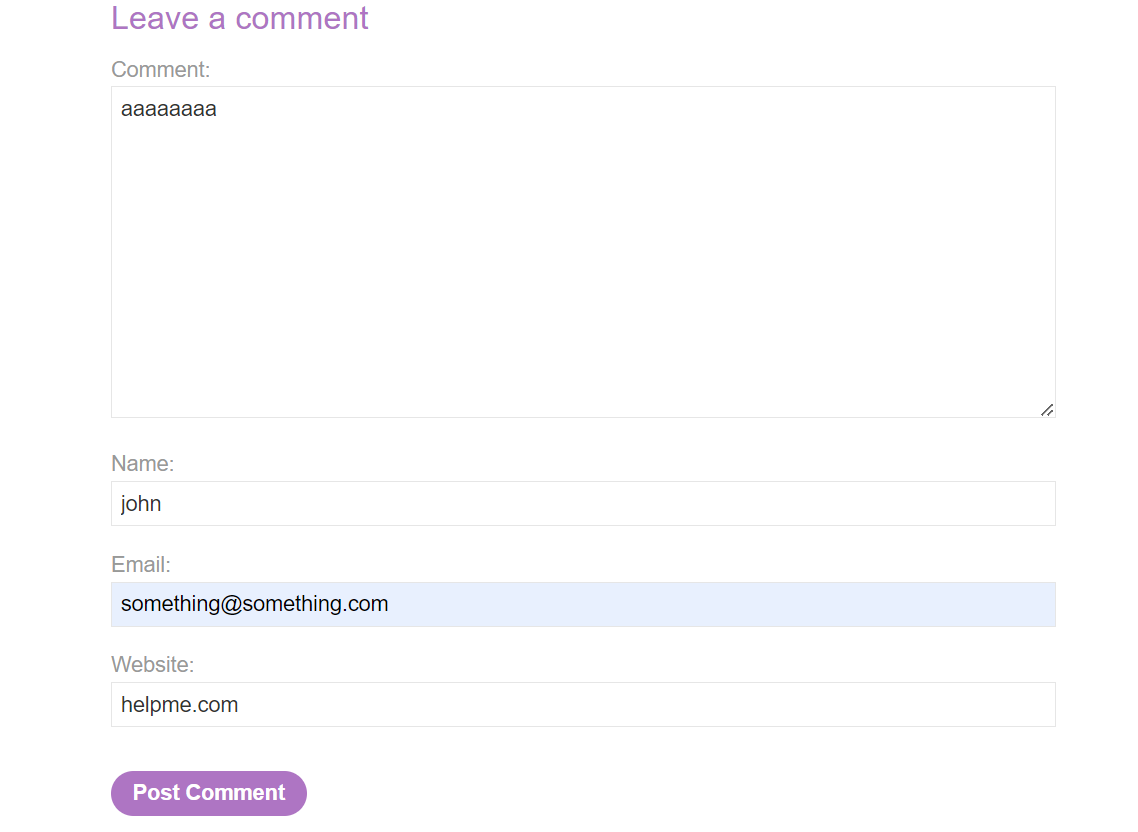
Now when we go back to the comment section, this is what we see:
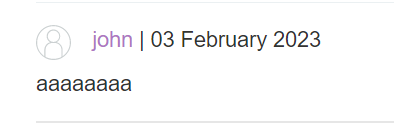
And the page source looks like this:
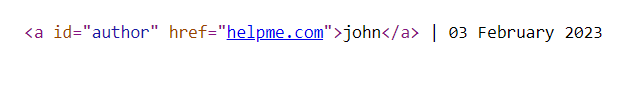
Interesting! When we click on the name “john”, we are taken to the page https://YOUR-LAB-ID/helpme.com. We see that what we entered in the website field ended up as the value of the “href” attribute. Perhaps we can enter something malicious in that field so when someone clicks the name of the author of the comment, they are taken to where they absolutely did not want to go, or even worse - they see a popup that says “1”!
Fun fact: href allows us to insert javascript by entering the word “javascript”, followed by whatever we want to happen next. Makes sense, right? So let’s try what happens when we post another comment and enter “javascript:alert(1)” in the website field:
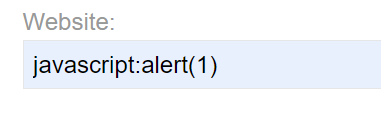
Let’s post it, open the comment section of the blog post again and click on the name “john” (or whatever you chose).
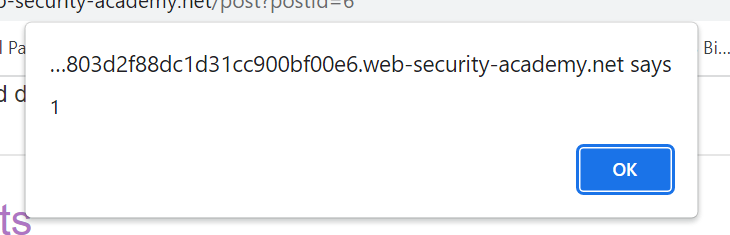
And there it is, the evil popup! Our work here is done for today…