Level: Apprentice
Today we will solve Portswigger’s “Basic SSRF against another back-end system” lab from their SSRF (server-side request forgery) series.
This is what we know:
This lab has a stock check feature which fetches data from an internal system.
To solve the lab, use the stock check functionality to scan the internal 192.168.0.X range for an admin interface on port 8080, then use it to delete the user carlos.
Okay, let’s run Burp and let’s go!
When we open the lab, we can see that it’s a web store with a lot of different items. As we know, we need to find the stock check feature, so let’s click on one of the items. At the bottom of the page we see what we need:

Let’s click “Check stock” and see what the request looks like in Burp. There we can see an internal IP address 192.168.0.1:

To make it look friendlier to the eye, we can also highlight the URL and press Ctrl+Shift+U to URL-decode it. Then let’s send this request to Intruder. Our goal is to find an admin interface on port 8080 and in order to do that we will scan the 192.168.0.X IP range.
First, we need to clear all the existing positions with “Clear §”, and then add a position marker only to the last octet of the IP address:

Next, in the “Payloads” tab, we need to choose “Numbers” as the payload type, and under “Payload options” let’s set the number range from 1 to 255 (since this is the range of each octet) with a step count of 1.
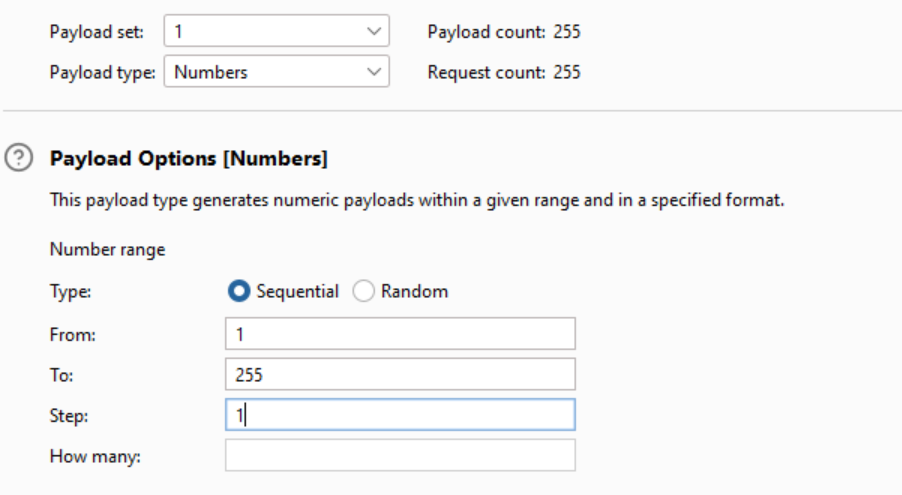
Now we can run the attack. When we look at the status codes of the requests, we can see that most of them are 500 (Internal Server Error). However, when we sort the results by status, we can see that there is one result with a status code of 404. Interesting… This indicates that the server behind that IP address is running (great news!), but that specific page doesn’t exist.
All we need to do now is access the admin interface. Let’s send the request from Intruder to Repeater and see what we can do. In this lab, for the sake of simplicity, we can find what we are looking for in a directory called /admin, so let’s change the address accordingly.
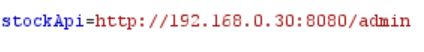
In real-life scenarios, finding directories will most probably not be this straightforward. You can play around manually a little bit to see if you get lucky, but a more efficient way both time-and energy-wise would be bruteforcing using Burp Intruder.
Now, when we go through the response for the request above we see that, in addition to the fact that this page indeed exists, there is a URL ending with /admin/delete?username=carlos. Well, that looks suspiciously like something we need in order to erase Carlos from existence.
We paste that URL in the correct place:

Let’s send the request, et voilà, Carlos is no more and we have solved the lab!





